Why hardware?
The fundamental concept behind Garrison SAVI® is that risky content – HTML, javascript, PDFs and more – is converted to raw pixels to sanitise it. But with security, the details matter.
Garrison SAVI® not only transforms the risky content to something safe, it then verifies that only the safe format is ever transferred across the isolation boundary – a barrier that is fully enforced in hardware. Garrison is one of the only commercially available solutions to conform to trusted authoritative security patterns.
For example see the data import guidance from the UK’s National Cyber Security Centre (a part of GCHQ).
Doing this at all is hard. Doing it in a way that is robust against efforts by sophisticated hackers to subvert it is really hard. Achieving all that and delivering a usable and scalable enterprise or cloud solution is a very significant challenge. This is the problem that Garrison SAVI® solves.
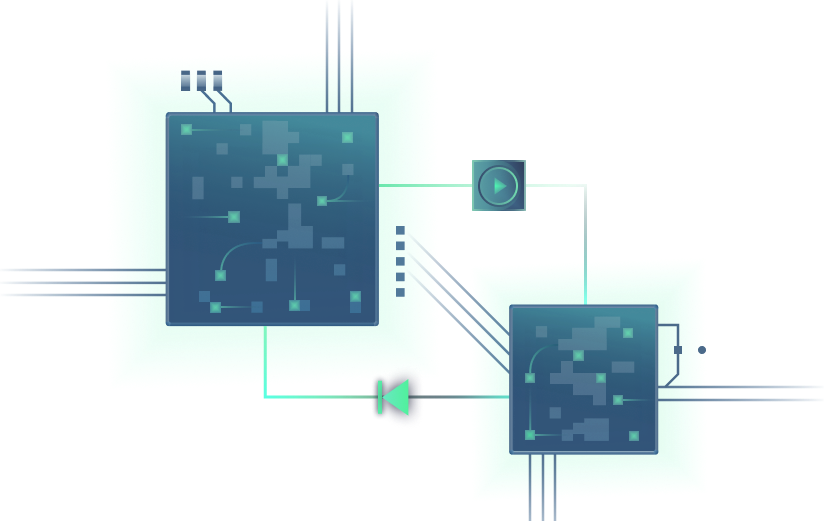
To meet the challenge, Garrison turned to the power of hardware. Garrison SAVI® technology is a simple concept that takes advantage of the incredible power of the Arm devices that power the world’s mobile phones and tablets. By chance, it turns out that these devices are a perfect fit for secure remote browsing. Garrison SAVI® uses two Arm chips working as a pair. One of these two chips acts essentially as a tablet. It runs a browser (and other apps) for consuming internet content. The pins of that Arm chip which would normally be connected to a display are instead connected to the camera input pins of the second Arm chip – which acts essentially as a camera. The ‘camera’ chip watches the screen output of the ‘browser’ chip, compresses what it sees, and sends it over the network to be displayed to the user on their endpoint device.
If the ‘browser’ chip gets compromised by a malicious website, it will end up running malware. But the hardware design verifies that the only thing it can send to the ‘camera’ chip is raw bitmaps. As a result, the ‘camera’ chip is safe from compromise – in turn isolating the user’s endpoint device from any harm.
Installed in the data centre, the Garrison SAVI® Isolation Appliance contains hundreds of Arm chips, supporting large numbers of concurrent sessions to deliver a highly scalable enterprise or cloud solution.
You might expect that this sort of hardware security was only suitable for military or other national security applications. But by exploiting the price-performance of Arm chips designed for the mobile market, Garrison SAVI® makes ultra-high security available at pricing in line with standard commercial security controls.
There are other remote browsing solutions. We wish our competitors well. But if the pricing is comparable, would you choose a solution that was based on software (with all the inherent security vulnerabilities that brings) or a solution that’s secured at the hardware level?

Inevitably, with any secure remote browsing solution, at some point the browser will be compromised. After all, that’s the whole point – if you weren’t worried about browser compromise, you wouldn’t deploy secure remote browsing in the first place.
What is critical however, is that the compromised browser should be isolated – able to transmit out only the guaranteed safe data required for transmission to the user.
Software-based remote browsing solutions rely on virtual machines or containers to keep compromised browsers isolated. But there is growing recognition in the security community that virtual machines are not the impenetrable boundary they were once claimed to be. Virtual machine vulnerabilities and escape exploits are being discovered at an ever-increasing rate. The situation for containers is even worse. And for cloud-based software solutions, the answer is usually containers – the cloud platforms themselves (AWS, Azure, etc) already use virtualisation in their IaaS implementation, meaning that SaaS services such as remote browsing cannot put another layer of virtualisation on top. Providers therefore use containers (which can be run within virtual machines) to try and isolate compromised browsers. But containers share a kernel with the host operating system – and any kernel exploit will give malware in a container access to the host.
If malware can break out of the VM or container, it can send malicious instructions to the user’s device. And of course, malware could find ways to persist in low-level code in order to attack the next user.
At best, software-based solutions will have provided a temporary barrier for an attacker to overcome. By contrast, Garrison provides true hardware-level isolation for compromised browsers – making secure remote browsing truly secure.
To understand the user experience challenge, you first have to understand the core principle of secure remote browsing. Anyone can claim to have a secure remote browsing solution – but what makes secure remote browsing different from traditional web security technologies such as proxies?
The key to secure remote browsing is that risky web content must be transformed to a guaranteed safe format – and that only guaranteed safe data is delivered to the user’s device. But what constitutes ‘guaranteed safe’? Great care needs to be taken here – almost every data format once believed to be safe has formed the basis for security exploits. Even PDF documents were once thought to be safe!
For visual data, what is truly safe is a fixed format, fixed frame rate series of raw bitmaps. This constitutes a series of fixed size memory buffers within which any contents constitute a perfectly valid bitmap. For secure remote browsing, visual web content needs to be transformed to a series of raw high definition bitmaps, at a sufficiently high frame rate to provide a smooth user experience. But a stream of high definition bitmaps is a high bitrate raw video stream – typically more than 1Gbit/s per user. This data needs to be aggressively compressed before it can be sent over a network. And high definition video compression is computationally very demanding, making huge infrastructure demands on any purely software-based solution.
So one option is to buy huge numbers of servers, making for a very expensive solution. Or more likely, to under-provision infrastructure and end up with an unacceptably poor user experience.
The other option is to compromise on the security model – for example, passing Internet content such as images and video through in their raw form, exposing the device to the associated risks.
By contrast, Garrison does not compromise on either security or the user experience. Each Garrison SAVI® Isolation Appliance incorporates dedicated high definition video compression silicon capable of compressing hundreds of gigabits of media data each second, providing a much more cost-effective approach to compression than pure CPU. The result is an excellent user experience that does not degrade when the system scales to large numbers of concurrent users – while maintaining the critical core security model.

SAVI Nodes are recycled between users on demand, meaning that a single Garrison SAVI® appliance can serve thousands of users. But what if there is malware that has persisted since the last user? With Garrison Secure Reboot technology, that’s not an issue. When the chips in each SAVI Node are recycled to a new user, Garrison ensures that they are delivered to the new user in a guaranteed clean state.
That means ensuring that any malware which might have compromised the chips in the node is unable to persist when the node is assigned to another user. Malware often works hard to try and persist – trying to hide even in low-level system firmware such as the BIOS.
Garrison Secure Reboot technology is implemented at the hardware level, involving a full power-cycle and a boot management bus that protects – again at the hardware level – against attempts to persist across power cycles even at the bootloader or BIOS level.

Garrison SACS® is Garrison’s Silicon Assured Content Sanitisation technology.
Garrison SACS® enables copy-and-paste and printing as securely as Garrison SAVI® provides the browsing. Garrison SACS® technology sanitises text and image formats by converting them to ‘known good’ format and using hardware-based verification to ensure that only that known good format can be transferred to the native device.
With Garrison SACS® the browsing workflow continues uninterrupted for copy-and-paste and printing while maintaining Garrison’s ultra-high level of security.